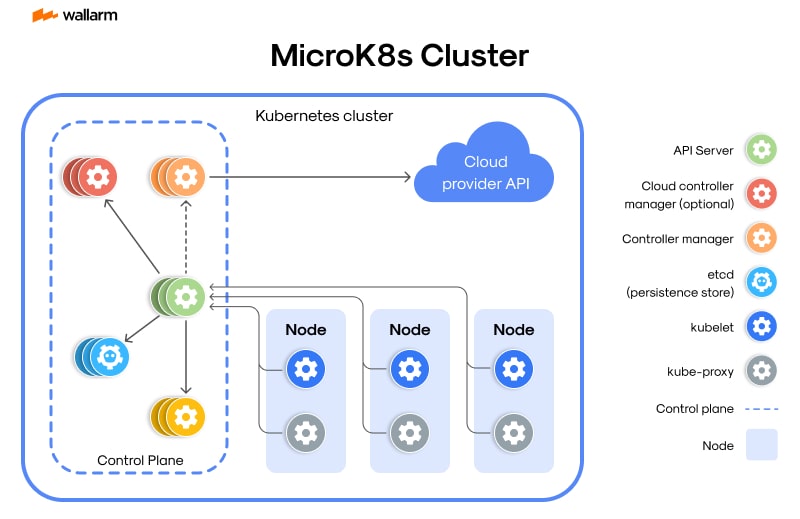
What is K3s and MicroK8s 2?
K3s and MicroK8s 2 are two popular lightweight Kubernetes distributions designed for resource-constrained environments and IoT devices. They provide a robust and efficient way to deploy and manage containerized applications. In this article, we will explore the disaster recovery workflow for K3s and MicroK8s 2, focusing on backup and restore operations.
Main Features of K3s and MicroK8s 2
K3s and MicroK8s 2 offer several key features that make them ideal for disaster recovery and backup operations:
- Lightweight and resource-efficient
- Support for ARM and x86 architectures
- Easy to install and manage
- Robust security features
Backup and Restore Operations
Creating a Backup Repository
To create a backup repository for K3s and MicroK8s 2, you can use the built-in backup tools or third-party solutions. Here are the general steps:
- Install and configure the backup tool
- Define the backup repository and retention policies
- Configure the backup schedule and frequency
Example Backup Repository Configuration
| Repository Name | Retention Policy | Backup Schedule |
|---|---|---|
| daily-backup | 30 days | daily at 02:00 |
Restoring from Snapshots
Overview of the Restore Process
Restoring from snapshots involves several steps, including:
- Identifying the snapshot to restore from
- Verifying the integrity of the snapshot
- Restoring the snapshot to the desired state
Example Restore Command
k3s restore --snapshot=daily-backup-20230220
Dedupe Backup Repositories with Encryption at Rest
Benefits of Dedupe and Encryption
Dedupe and encryption provide several benefits for backup repositories, including:
- Reduced storage requirements
- Improved data security
- Compliance with regulatory requirements
Example Dedupe and Encryption Configuration
k3s backup --dedupe --encrypt --key-file=/path/to/key
Conclusion
In this article, we explored the disaster recovery workflow for K3s and MicroK8s 2, focusing on backup and restore operations. By following the guidelines and best practices outlined in this article, you can ensure the integrity and availability of your Kubernetes deployments.